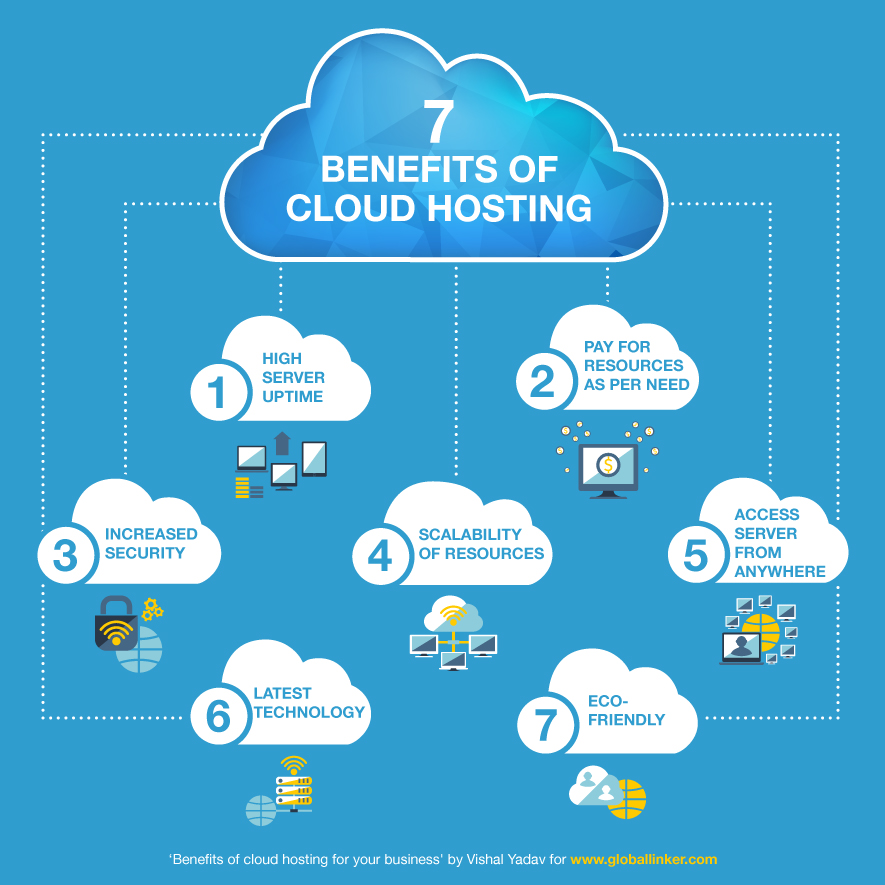
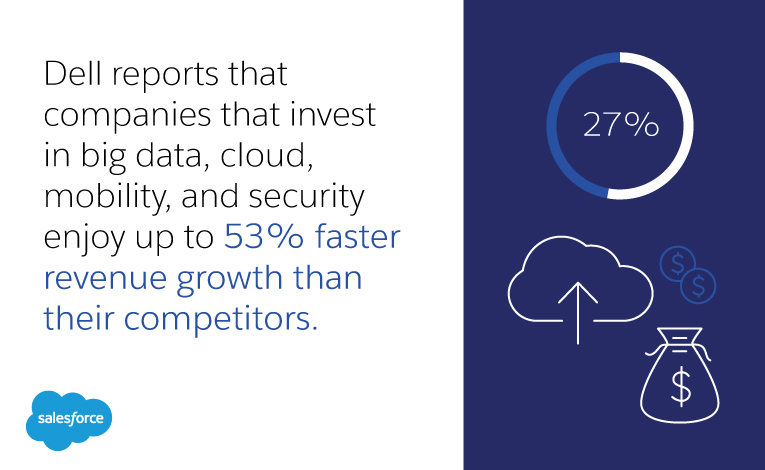
About It Support Charlotte
For some people, maintaining your privacy is crucial. You may desire the benefits of a social support system however fret about needing to disclose what ails you to accomplish this.
They may initially join online neighborhoods or seek out local assistance groups that are much less formal. At Highland Springs we can be your first action in finding an assistance system.
Our Charlotte It Outsourcing Statements
Interactive computer support might also be done over the phone, e-mail, or conversation. Working with MSPs that supply computer support as well as services can help your service in managing some computer system problems you might run into.
The managed service carrier can take care of all your IT solutions, providing you more time to run your service. This means you do not need to worry any longer concerning coordinating with your IT group when something goes incorrect. Rather, you can focus on more crucial jobs while the support services maintain your computers running seamlessly.

Some consumers expect to receive an action within the day while others anticipate a reply within a hr. Having claimed this, it is important that customer worries are cared for quickly to ensure their loyalty to your service. Improving customer assistance is crucial to your success. If individuals do not obtain the support they anticipate, they're most likely to go to your rivals.
The Single Strategy To Use For Charlotte It Outsourcing


The finest way to protect your organization against cyberattacks is by working with a trusted IT support firm that has experience in taking care of cybersecurity concerns. When you select a credible IT support company, you can feel confident that your data as well as details will certainly remain secure. Your service will remain to operate efficiently if you have access to the right resources.
Unknown Facts About It Company Charlotte
Staying abreast of the latest developments is critical to safeguard your organization. IT sustain groups are encountering lots of obstacles in securing organizations' networks.
A skilled IT support team can recommend on implementing the needed adjustments in your business. They can also monitor your network and also servers to make certain every little thing is working appropriately. With over 20+ years of experience offering the technology sector, we understand what it requires to grow your business. Get in touch with us today for more information about our solutions! Gary Mc, Cauley is accountable for monitoring as well as sales of Exter, Networks National Accounts.
Both internal and outsourced IT over at this website can hold its advantage official source over the various other. In this guide, we will check out in-house and also outsourced IT advantages and disadvantages, advantages and also downsides: Internal IT sustain is having an IT department or IT expert functioning inside your business premises. You will certainly use the individual or team, and you have full control over them.
Not known Incorrect Statements About Charlotte It Outsourcing
While an outsourced IT company can do this using a remote session, it's never ever rather the like existing in person. Having the ability to see an issue before you comes to be a big benefit when the issue is with hardware rather than software application. The influx in remote functioning as well as cloud computer has actually taken the sparkle off this benefit.
Utilizing individuals that are in line with your firm worths will boost productivity, as well as any kind of human resources problems can be dealt with on website promptly. When you utilize somebody in-house, you can tailor the training for them. The training can be to enhance their IT skills or training that the entire firm does.
Get a rapid quote for IT sustain as well as discover exactly how much it would certainly cost your business. The disadvantages as well as downsides of in-house IT sustain consist of: Greater cost No IT support throughout yearly leave IT sustain just covers 9-5, not nights or weekend breaks Required to quickly replace IT workers Someone can't understand or do every little thing High level of trust fund Resistance to change Here's why internal IT didn't fit one of our customers: Transcript: When we got business, when we initially began, we had an in-house IT support individual that was actually proficient at his role, however the trouble was we couldn't obtain him to be 24/7, so we constantly battled when we had any type of problems.